VPN Encryption (All You Need to Know)

VPN encryption feels like a literal godsend to many people, and it’s not hard to see why. It helps you easily secure your online data against cybercriminals and abusive government and ISP surveillance.
But did you ever wonder how VPN encryption actually works? Well, if you’d like to learn about that, you’ve come to the right place. We’ll be discussing encryption keys, algorithm types, VPN cipher types, VPN encryption protocols, and more.
Table of contents
What Is VPN Encryption?
At its core, encryption is a way of converting data from a readable format to an encoded, unreadable format with the help of an algorithm. Said encoded format can only be decoded with the right decryption key.
Going off of that statement, VPN encryption can be defined as a means of encrypting plaintext data (like your online traffic) to make sure it shows up as indecipherable gibberish to anyone who tries to monitor it (like your ISP, for instance).
Why Is VPN Encryption Important?
For one, VPN encryption lets you protect sensitive data (like credit card numbers, bank account details, and login credentials) from cybercriminals since they won’t be able to eavesdrop on your Internet connections when you use public WiFi.
Besides that, VPN encryption also makes sure your Internet activities can’t be monitored by your government, ISP, and advertisers.
How does that help? Well:
- It prevents governments from forcing censorship down your throat, or even putting your life in danger if you happen to end up in legal trouble in Middle Eastern countries where certain online activities are illegal.
- It protects you from unfair DMCA notices, huge fines, and even jail time if you are downloading torrents.
- VPN encryption prevents your ISP from throttling your bandwidth since they can’t see what you do online.
- Encryption also keeps advertisers at bay by making it less likely for you to get spammed with “personalized” ads or to have your online data sold to advertisers by your ISP.
How Does VPN Encryption Work?
VPN encryption is the process of securing the data within the VPN client-VPN server tunnel to make sure it can’t be exploited by anyone.
Basically, when you run a VPN client and connect to a VPN server, your connection requests are encrypted before they are sent to the server.
Then, they are decrypted by the server, forwarded to the Internet, and the requested data is encrypted once more when the server receives it before it’s sent back to your device. Once received, the data is decrypted by the VPN client so that you can view it.
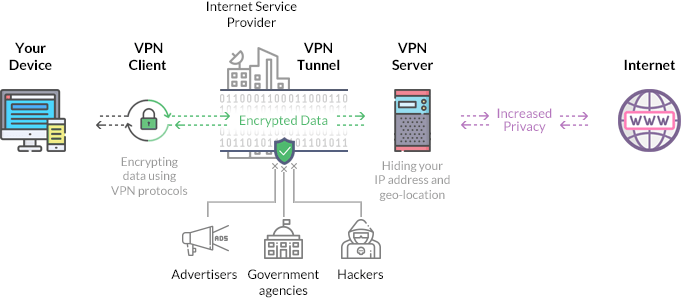
Still, to get a more in-depth understanding of how VPN encryption generally works, you need to learn about things like:
- Encryption keys
- Encryption algorithms
- VPN encryption ciphers
- VPN encryption protocols
- Handshake encryption
- HMAC authentication
- Perfect Forward Secrecy
What Are Encryption Keys?
A VPN encryption key is a randomly-generated string of bits that’s used to encrypt and decrypt data. Each encryption key is generated in such a way as to ensure it’s unique. The length of an encryption key is calculated in bits – normally, the longer the key, the stronger the encryption.
The size of encryption keys is very varied. For example, they can be 1-bit, allowing for just two possible combinations, or 256-bit, allowing for a total of 1.1 times 10^77 combinations.
To give you an idea of what that means, it’d take the Sunway TaihuLight (a supercomputer, and one of the most powerful – if not the most powerful – computers in the world) around 885 quadrillion years just to brute force a 128-bit encryption key.
Two types of encryption keys are used in the encryption/decryption process – the Private Key and the Public Key. They are mathematically related, as any kind of information that is encrypted with a Public Key can only be decrypted with the Private Key associated with it.
Also, the Public Key is normally available through a public directory, while the Private Key (like its name implies) remains confidential and is only known by the key owner.
Types of Encryption Algorithms
When discussing VPN encryption types, it’s important to make the difference between encryption algorithm types and encryption cipher types. Right now, we’ll be discussing the algorithms types, and we’ll go over ciphers in the next section.

Nowadays, encryption algorithms generally fall into two categories:
- Symmetric Encryption – A symmetrical encryption algorithm relies on a Public and Private Key that are identical. It’s usually considered a “fast” algorithm. One example of symmetric encryption is the AES encryption cipher.
- Asymmetric Encryption – This type of algorithm (also known as Public-Key Cryptography) uses different keys for the encryption and decryption processes. While it can be convenient, it’s also very risky since a Private Key that is lost can normally not be restored. A good example of asymmetric encryption is the RSA (Rivest-Shamir-Adleman) protocol.
What Are VPN Encryption Ciphers?
An encryption cipher is an algorithm that’s used for performing the encryption and decryption process. Unlike encryption keys that can’t be realistically cracked, encryption ciphers might have weaknesses that makes it possible to break the encryption.
Luckily, that kind of security issue is easily avoided by using a complex cipher alongside a strong encryption key.
Before we discuss what types of VPN ciphers VPN providers might use, we need to mention a few things – the name of a VPN encryption cipher will normally be accompanied by the length of the key (AES-128, for instance).
It’s also worth noting that when people refer to VPN encryption algorithms in most cases, they’re usually referring to encryption ciphers – not the symmetric/asymmetric algorithms we mentioned above. So, if you see someone talking about the Blowfish algorithm, it’s okay to assume they’re referring to the Blowfish cipher. The same can be said when people talk about VPN encryption types – generally, they’re talking about the types of encryption ciphers that are available.
With that out of the way, here are the main types of encryption ciphers you will see VPN providers use:
- The Blowfish Cipher – Blowfish is normally accompanied by a 128-bit key. While it is rather safe, many online users are worried about how reliable it is given that the cipher’s designer (Bruce Schneier) has stated the following in a 2007 interview about Blowfish: “At this point, though, I’m amazed it’s still being used.”
- The Twofish Cipher – This is the successor of Blowfish. The main difference is that Twofish has a 128-bit block size instead of the 64-bit one Blowfish has, meaning it’s not vulnerable to birthday attacks. Bruce Schneier also recommends using Twofish over Blowfish.
- The AES Cipher – AES can have 128-bit, 192-bit, and 256-bit keys. AES is very popular with VPN users thanks to its NIST certification, and the fact that the US government also uses it.
- The Camellia Cipher – Camellia is allegedly as good as AES. It’s fast, and it supports 128-bit, 192-bit, and 256-bit keys. However, since it hasn’t been thoroughly tested against potential weaknesses too much yet, and due to its lack of certifications, AES tends to be picked over it.
- The 3DES Cipher – Triple DES (3DES; also known as TDEA/Triple DEA) is basically the Data Encryption Standard (DES) being used three times. It’s slower than Blowfish, and it only supports 56-bit, 112-bit, and 168-bit keys. Also, like Blowfish, it has a 64-bit block size, making it susceptible to birthday attacks. One important detail worth mentioning is that this cipher has officially been retired, and its usage will be prohibited after 2023.
- The MPPE Cipher – MPPE stands for Microsoft Point-to-Point Encryption, and it’s a cipher often used for PPTP connections and dial-up connections. The cipher supports 40-bit keys, 56-bit keys, and 128-bit keys.
The RSA cipher is another algorithm that can be used for secure online communications, but we’re mentioning it here and not adding it to the list above because most VPN provider use RSA for encryption handshakes since the cipher is relatively slow. In general, RSA isn’t used for directly encrypting user data due to that. Also, it’s worth mentioning that the 1024-bit RSA key is no longer considered safe, and security experts advise using the 2048-bit or 4096-bit one instead.
What Is Encryption Handshake?
A “handshake” represents that automatic communication between two communicating devices. Basically, it refers to how the VPN client and VPN server establish the encryption keys that are used for communication (encryption and decryption in this case).
During the handshake (usually a TLS/SSL one), the client and server:
- Generate the encryption keys.
- Agree which VPN protocol will be used.
- Select the appropriate cryptographic algorithms.
- Authenticate each other with the help of digital certificates.
Like we mentioned above, RSA is normally used for encryption handshakes. However, it’s also possible for a VPN provider to use the ECDH (Elliptic-curve Diffie-Hellman) or DH (Diffie-Hellman) key agreement protocol as well. ECDH is usually more ideal because DH tends to re-use a limited set of prime numbers, making it more susceptible to being cracked by the NSA.
What Is Perfect Forward Secrecy (PFS)?
Perfect Forward Secrecy (also called Forward Secrecy) is a feature of various key agreement protocols (a combination of RSA and DH or ECDH, usually) that makes sure your session keys aren’t compromised even if something happens to the Private Key of the server you’re connecting to.
In case you’d like to learn more about PFS, feel free to check out our article on it.
What Is HMAC Authentication?
HMAC authentication stands for Hash-Based Message Authentication Code, and it’s a Message Authentication Code (MAC) that’s used to check the data integrity and authentication of a message at the same time to make sure it hasn’t been modified by any third-parties.
VPN providers usually use the SHA-2 (Secure Hash Algorithm 2) cipher for HMAC authentication since it supports 224-bit, 256-bit, 384-bit, and 512-bit hash values, making it far more secure than SHA-1.
What Are VPN Encryption Protocols?
Simply put, a VPN protocol is a set of instructions that are used when a secure connection between two devices is established. In this case, the two secure devices would be the device you run the VPN client on, and the VPN server you connect to.

VPN providers normally use multiple types of VPN protocols when negotiating secured connections. The more decent providers will actually let you choose which VPN protocol you will use when connecting to the VPN server.
Normally, these are the most widely-used VPN protocols at the moment of writing of this article:
- PPTP – A relatively high-speed VPN encryption protocol. The main problem with it is the fact that it has poor security – not to mention it was likely cracked by the NSA too.
- L2TP/IPSec – On its own, L2TP provides no encryption, which is why it’s always paired up with IPSec. Together, they make for a pretty secure protocol (especially if it uses the AES cipher). There have been claims that the NSA has cracked or weakened this VPN encryption protocol, but there is no proof to back them up.
- IPSec – IPSec is a secure network protocol suite that’s used to encrypt data packets which are sent over an IP network. It features high security, and it can encrypt traffic without the end point application being aware of it. In VPN technology, IPSec is often used alongside L2TP and IKEv2.
- IKEv2 – IKEv2 is relatively fast, stable, and safe (if a cipher like AES is used). Still, IKEv2 can be hard to implement on the VPN server side, so an inexperienced VPN provider could make mistakes which can result in security problems.
- OpenVPN – An open-source protocol, OpenVPN is very secure and configurable. Its only downside seems to be the fact that using it with strong encryption ciphers can sometimes slow down connection speeds.
- SoftEther – Despite being a newer VPN encryption protocol, SoftEther has quickly become popular with VPN users due to the fact that it’s very secure, stable, and surprisingly fast.
- SSTP – This protocol is often compared to OpenVPN since it uses SSL 3.0, thus allowing it to bypass censorship by using port 443 (the HTTPS traffic port). Despite that, SSTP isn’t as popular as OpenVPN because it’s not open-source.
- WireGuard® – Wireguard is a new, open-source VPN protocol. It only uses a single cryptographic suite, so it’s less likely to have security holes. Despite how “young” the WireGuard protocol is, it has been quickly accepted by online users, and even managed to catch the attention of main Linux developer Linus Torvalds who called it a “work of art.”
When it comes to security, OpenVPN is considered to be the standard nowadays. However, that doesn’t mean it’s the only choice. WireGuard and SoftEther are very good alternatives that is often much faster than OpenVPN, and offer a decent level of security too.
In case you’d like to learn more about each VPN protocol, feel free to check out our in-depth guide.
What’s the Best VPN Encryption?
It’s difficult to say since there isn’t a simple, clear-cut answer to this question. What defines the “best encryption” for you depends on how much you want to secure your online data and traffic.
Overall, here are the main things you need to look for if you want to make sure you’re getting the most secure online experience:
- A long encryption key, at least 128-bit in size.
- Reliable key exchange protocols, like ECDH or RSA-2048.
- Strong VPN ciphers like AES, Twofish, or Camellia.
- Powerful VPN encryption protocols like OpenVPN, SoftEther, and IKEv2.
- A SHA-2 cipher for HMAC authentication – ideally 256-bit, 384-bit, or 512-bit.
- Perfect Forward Secrecy features.
How to Test VPN Encryption
Judging by how complicated VPN encryption can be as a subject, you’d think that testing it would be even harder. Luckily, that’s not the case.
Here are the steps you need to follow to test VPN encryption quick and easy:
- Install Wireshark – a tool that can monitor the status of a VPN’s encryption.
- Run Wireshark, and then start the VPN client and connect to a server.
- Choose WiFi or Ethernet as the network interface you want to record.
- Next, start recording.
- Under “Protocol,” choose “OpenVPN.” You can choose a different VPN encryption protocol if you want as well.
- Now, right-click on the OpenVPN packet, and either monitor a UDP or TCP stream.
- As long as the stream is displayed as gibberish, that means the VPN encryption is working well.
If you’d like to try out another method, do the following:
- Install Glasswire.
- Run the software while connected to a VPN server.
- Browse the web, and download some files.
- Now, head over to the “Usage” tab.
- Select the “App” section.
- Find the VPN you’re using, and check out what the VPN encryption status says.
For the best results, we recommend trying out both methods.
Do All Providers Offer VPN Data Encryption?
Not exactly – free VPNs are quite the gamble in this case since they might claim they offer encryption when in reality they don’t secure your data at all.
What’s more, even when free VPNs do manage to provide encryption, it will usually just be a weak cipher, a small encryption key, and less secure VPN encryption protocols like PPTP and L2TP (which, like we already mentioned, has no encryption on its own unless it’s paired up with IPSec).
Another problem you will have to deal with is the fact that free VPNs are likely to have poorly-configured VPN encryption, according to security experts. Also, it seems that free VPN users are more likely to get hacked by cybercriminals as well.
Bottom line – if you want real Internet security, stick to a reputable paid VPN service.
Need a Reliable and Highly Secure VPN Service?
CactusVPN is exactly the service you need then. We offer strong AES encryption, DNS leak protection, a Kill Switch feature, and a choice of up to six VPN protocols: OpenVPN, SoftEther, IKEv2, L2TP/IPSec, PPTP and SSTP.
Your Privacy Is 100% Protected
You don’t need to worry about your online privacy being compromised when using CactusVPN because we enforce a strict no-log policy at our company. That means we don’t record anything you do on the Internet, since that’s only your business and nobody else’s.

Special Deal! Get CactusVPN for $3.5/mo!
And once you do become a CactusVPN customer, we’ll still have your back with a 30-day money-back guarantee.
“Can VPN Encryption Slow Down My Speeds?”
There is a chance that might happen. It all depends on how strong the VPN encryption you use is. For example, using the OpenVPN protocol with AES-256 is likely to result in some online connection slowdown because it uses up a lot of CPU power.

Of course, you should know that there’s no guarantee you will experience slowdowns 100% of the time. Sometimes, it might not happen, or it might barely be noticeable (like a 1-2 Mbps loss in speed or so).
If you’d like to know more about this topic, feel free to check out this guide we wrote about VPN speed.
Conclusion
VPN data encryption is used to secure user traffic and information, essentially making it surveillance-proof to protect it from ISP monitoring, cybercriminals, and government surveillance.
The way it works is this: The VPN client first encrypts the connection requests, and sends them to the VPN server which decrypts them and forwards them to the web. Then, the received data is encrypted by the VPN server and sent to the VPN client, which then decrypts the received info for you.
A lot goes into how VPN encryption works – how long the encryption key is, what type of encryption algorithm and cipher is used, what type of encryption is used for the authentication process, what kind of key exchange protocols are used, and what VPN protocol(s) is(are) used.
Overall, you should pick a VPN provider that offers VPN protocols like OpenVPN, IKEv2, and SoftEther, ciphers like AES and Camilla, authentication encryption over 256 bits, and handshake encryption like RSA-2048.
“WireGuard” is a registered trademark of Jason A. Donenfeld.
 Introduction to VPN
Introduction to VPN
 What Is PFS (Perfect Forward Secrecy)?
What Is PFS (Perfect Forward Secrecy)?
