Can You Be Tracked If You Use a VPN?

VPNs are an excellent way to protect your online privacy and data. Besides unblocking geo-restricted content, that’s probably the second main reason people use VPNs in the first place.
There’s just one thing that’s probably on your mind – can you be tracked if you use a VPN?
Let’s find out in this quick article.
Can You Be Tracked If You Use a VPN?
Yes and no.
No, your web traffic and IP address can’t be tracked anymore. The VPN encrypts your data and hides your IP address by routing your connection requests through a VPN server. If anyone tries to track them, they’ll just see the VPN server’s IP address and complete gibberish.
Yes, there still are some ways your online browsing might be tracked even if you use a VPN:
1. Malware
Malware is malicious software and code that were programmed to take over a network or device. Unfortunately, VPNs can’t protect you from malware infections. They can only protect your online data, not your hardware.
The best a VPN can do is offer a firewall-like feature that blocks connections to malicious domains. But even that’s not enough to stop malware infections. You might just accidentally download a malicious file from a legit site or interact with a phishing email, for example.
If that happens, hackers can use the malware to track everything you do – what you browse online, what passwords you type, what files you save to your hard drive, what you talk with your friends, etc.
SOLUTION
The best line of defense against malware is a strong anti-malware program (also called anti-virus software). If you’d like some recommendations, try Malwarebytes or ESET.
Besides that, do the following to further protect your data from malware attacks and phishing:
- Use password managers like LessPass and Bitwarden.
- Enable 2FA (Two-Factor Authentication) or MFA (Multi-Factor Authentication) on all your accounts.
- Use script blockers like uMatrix and uBlock Origin.
- Use anti-phishing browser extensions like NetCraft, MetaCert, and PhishDetector. Alternatively, use Stanford’s Anti-Phishing Browser Extensions.
- Follow our anti-phishing protection tips.
2. Cookies
Cookies are small text files that websites place on your device whenever you visit them. Most cookies are harmless and necessary to help sites run well. However, some persistent cookie and third-party cookies are pretty bad for your privacy since they let sites and advertisers track your online preferences and behavior.
Due to how cookies work, VPNs can’t protect you from them. They’re not programmed to intercept files that download to your device, after all.
On the plus side, VPNs should protect you from ISP supercookies – tracking files that are stored on your ISP’s servers, and get inserted into your data packets when you go online. Since a VPN encrypts your traffic, your ISP shouldn’t be able to insert supercookies into it anymore.
Besides that, VPNs should theoretically stop hackers from intercepting your cookies and creating forged ones over unsecured WiFi by encrypting your traffic.
SOLUTION
Clear your cookies whenever you use a VPN. Here are some guides for the most popular browsers:
Besides that, you should also use incognito/private mode in your browser (it automatically deletes cookies when you close a tab), the Cookie AutoDelete (Firefox, Chrome, Edge) and Self-Destructing Cookies (Opera) browser extensions, and CCleaner (a cool tool that removes cookies across all platforms, and only costs around $25 per year).
3. Browser Fingerprinting
This is a tracking method websites use to monitor visitors by linking behavior patterns to them. Browser fingerprinting does that by assigning a unique identifier to you every time you visit a site. Said fingerprint can contain a lot of data – your time zone, screen resolution, web browser and OS version, system fonts, etc.
For a complete list of all the data browser fingerprinting collects about you, check out Device Info.
Unfortunately, browser fingerprinting is a pretty accurate tracking method. According to the EFF’s research, only one in 286,777 other browsers will share the same fingerprinting with a different user. So, your own fingerprint has a very good chance of being unique and standing out.
Because so much data is collected, a VPN can’t stop websites from tracking you with browser fingerprinting. The most it can do is hide your IP address, but that won’t really make your fingerprint less unique.
SOLUTION
Due to how it works, you can’t completely protect yourself from browser fingerprinting – unless you were planning on going off the grid and living in the woods any time soon.
Still, there are some things you can do to make your fingerprint less unique:
- Use Firefox since it blocks third-party fingerprinting resources. If you’re feeling up to it, use it with the user.js file from ghacks which is optimized for privacy (here’s the guide). Alternatively, use Brave since it has a built-in option to block all fingerprinting.
- Another option is to use the Tor Browser. You’ll have the same fingerprint as all users as long as you don’t change the default browser window size. Try using it with the Tor network disabled if possible since it’s not ideal for privacy.
- Use anti-fingerprinting browser extensions like Chameleon, Trace, or Canvasblocker. Try using just one, though. Otherwise, your fingerprint will be more unique.
- Disable Flash if you use older browser versions (newer ones should have it disabled by default).
- Disable JavaScript in your browsers. If you don’t want to do it manually, use uMatrix or NoScript. Just keep in mind some sites might not work properly without it.
- Use a VM (Virtual Machine) like VirtualBox or VMWare Workstation Player to emulate an OS within your current OS.
- Use a separate browser for each type of activity (Firefox for online banking, Chrome for streaming, Opera for Facebook, etc.). If you’re really hardcore and you can afford it, use a different device for each activity (maybe even burner devices).
4. Social Media
If you post personal information about you on social media (email address, phone number, whereabouts, etc.), someone can still track you even if you use a VPN. Please understand there’s no way a VPN can hide all the information you voluntarily make public.
Even worse, somebody could use all that information to dox you.
SOLUTION
For starters, don’t post (too much) personally identifiable information on social media. And definitely don’t tell random people on the web your current whereabouts. Do strangers really need to know your home is empty on weekend nights or that you’re very drunk at club X or bar Y?
What’s more, you should also take steps to make your social media account more private. Here are useful guides for most platforms:
5. VPN Logs
VPN logs contain data about how you use a VPN. There are two types of logs:
- Usage logs – They track your IP address, the sites you visit, and the files you download while using the VPN.
- Connection logs – They track timestamps, bandwidth usage, and your IP address while you use a VPN.
Both types of logs are bad for your privacy. After all, you’re using a VPN to stop ISPs, advertisers, and governments from tracking you. What’s the point of doing that if the VPN will track you instead?
SOLUTION
The best thing you can do is use a VPN that doesn’t keep any logs. If you’re looking for one, we have great news – CactusVPN stores zero logs.
6. VPN Leaks
A VPN leak is when your IP address or DNS queries leak outside the VPN encrypted tunnel. If that happens, anyone can track your web browsing and IP address even if you’re using a VPN.
There are different types of leaks:
- WebRTC Leaks
- DNS Leaks
- IPv6 Leaks
- Traffic Leaks
But they’re all equally disastrous for your privacy.
SOLUTION
Test the VPN to make sure it’s not leaking. You can use our testing guide to check for all leaks.
If the service is leaking, consider switching to a VPN that offers leak protection (like CactusVPN). You simply turn on the DNS leak protection switch from the CactusVPN app.
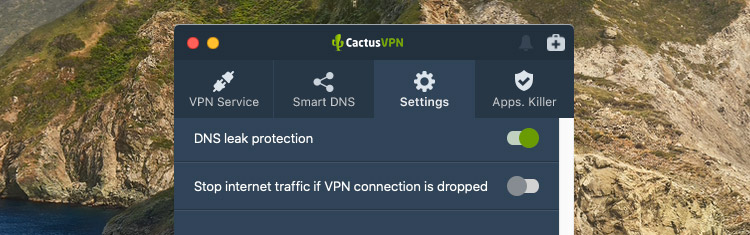
Also, here’s what else you should do to prevent leaks:
- Disable Teredo and SMHNR on Windows 10 (they cause DNS leaks).
- Disable IPv6 if your VPN doesn’t support IPv6 traffic.
- Disable WebRTC in your browser + use uBlock Origin.
- Enable the kill switch to protect yourself from traffic leaks.
Can VPNs Be Tracked by ISPs?
Contrary to popular belief, your ISP can actually track your VPN connection. It’s not invisible on their network.
Here’s what they can see:
- The source of the connection (your IP).
- The connection’s destination (the VPN server IP).
- How long you’re connected to the VPN.
- When you connect to the VPN.
- How much data you exchange with the VPN.
- What port your connection uses.
- Whether or not you use OpenVPN (if they use DPI).
So quite a lot of things. They’re only concerning if your ISP plans on blocking your VPN connection, though.
If they use IP blocking, you just need to connect to a different VPN server to get around it. And if they use DPI to drop or block your OpenVPN connections, just use obfuscation (available in CactusVPN through obfsproxy).
Do ISPs Usually Track VPNs?
Not really. They don’t have much of a reason to bother with tracking VPN connections across their networks. It’s a time investment that doesn’t really pay off.
However, there are some situations when they might focus on VPN connections:
- When the law forces them to do it. Basically, when governments ban VPN usage or censor certain sites (so they force ISPs to monitor and ban VPNs to make sure people don’t unblock them).
- When they’re worried their users are using VPNs to do illegal things (like illegally downloading copyrighted content).
- If they don’t like that their customers are using VPNs to bypass bandwidth throttling.
Can You Be Tracked If You Use a VPN and It Disconnects?
Yes, there’s a chance you can be passively tracked if that happens. And, unfortunately, VPN disconnects can happen no matter how good the service is.
Basically, if your VPN disconnects, and you visit a new site before it can reconnect, the site will track your real IP address. Also, your ISP will be able to track your connection to that site.
The best way to protect yourself from this is to use a VPN with a kill switch. That’s a feature that completely shuts off your web access when your VPN connection goes down. Your Internet access will only resume when the VPN connection is up and running again.
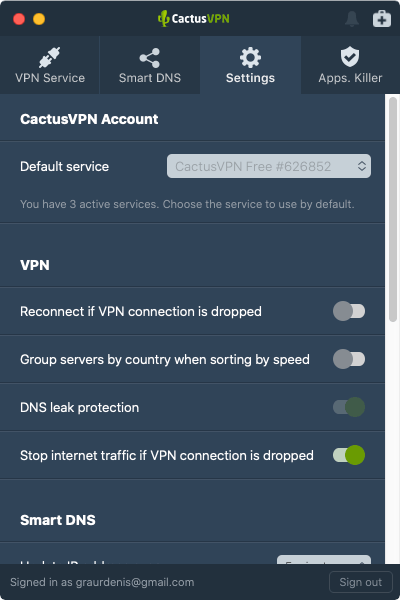
If you’re looking for a VPN with a kill switch but are bummed out you can’t find one, we have good news – CactusVPN offers a built-in system-level kill switch. Simply turn on the Stop internet traffic if VPN connection is dropped toggle from the CactusVPN app Settings.
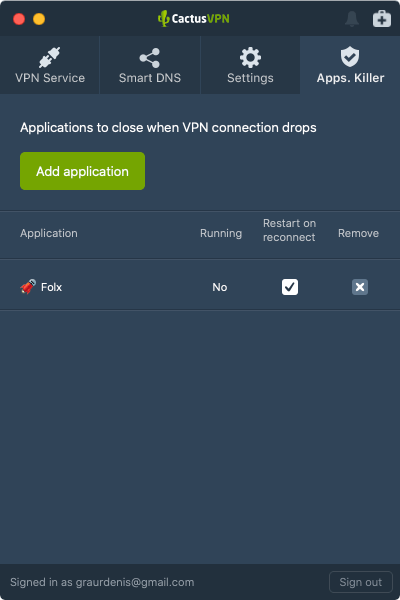
What’s more, we also offer an app-level kill switch, so you can selectively pick which apps can’t access the web when your VPN connection goes down.
Can You Be Tracked If You Use a Free VPN?
There’s a pretty good chance that might happen. While free VPNs are appealing, they’re not 100% reliable or trustworthy. We outlined why in our guide to free VPNs vs paid VPNs, but here are the highlights:
- Free VPNs might have poorly-configured encryption or protocols, resulting in VPN leaks.
- Free VPNs might sell your bandwidth to third parties.
- They could also log your data and sell it to advertisers.
- They might expose you to malware.
Can You Be Tracked If You Use a VPN Server in Your Country?
No, using a server in your country is just as safe as using a server in any other country.
What If You Live in a Country with an Oppressive Regime?
As long as the VPN doesn’t keep any logs, you’ve got nothing to worry about. Even if the authorities were to seize the VPN server, they wouldn’t be able to find any of your data on it. There isn’t any to begin with.
Need a Hard-to-Track VPN?
CactusVPN is the right tool for the job. We offer powerful encryption, secure protocols (OpenVPN, SoftEther, SSTP, IKEv2), DNS leak protection, a kill switch, and obfuscation.
Special Deal! Get CactusVPN for $3.5/mo!
And once you do become a CactusVPN customer, we’ll still have your back with a 30-day money-back guarantee.
Can You Be Tracked If You Use a VPN? What Do You Think?
Are there any other ways you might be tracked when you use one? If you know any, please tell us about them. Also, don’t forget to include ways to prevent or limit that kind of tracking.



